Introduction to Network ACL
Network ACL is a subnet-level security policy used to control the data flow into and out of the subnet. Users can precisely control the flow in and out of the subnet by setting outbound rules and inbound rules.
Network ACL is stateless. For example, if a user needs to allow certain access, they need to add the corresponding inbound rules and outbound rules at the same time. If only the inbound rules are added and no outbound rules are added, it will cause access anomalies.
ACL rules do not take effect on Outstanding Cloud Host, physical cloud hosts, ULB, VIP and instances implemented based on VIP architecture. Please refer to the console for specific information.
Associate Subnets
After creating a network ACL, the user can bind and unbind this ACL with any subnet under the associated VPC. Before binding a subnet, please make sure the rules in the ACL are correct, without affecting the normal communication of cloud resources in the associated subnet.
Outbound/Inbound Rules
Network ACL rules are divided into outbound rules and inbound rules. The update of user’s network ACL rules will be automatically applied to the associated subnet.
The maximum number of outbound/inbound rules that can be added is 50 each.
Network ACL rules include the following parts:
- Policy: Allow or Deny.
- Source IP/Destination IP: The subnet targeted by the outbound / inbound rule.
- Protocol Type: Support TCP, UDP, ICMP and GRE protocol types. You can choose ALL to specify all protocol types.
- Destination Port: The port range that can be filled in for TCP and UDP protocol types is 1-65,535. Other protocol types do not need to specify ports.
- Priority: The priority of the corresponding rule. The smaller the number, the higher the priority. The fill range is 1-30,000. Only one outbound/inbound rule can be created with the same priority.
- Application Target: The effective range of the ACL rule. Supports all resources within the subnet, and specific resources within the subnet. “All resources within the subnet” means that this rule applies to all resources in the subnet that bind this ACL (except for Outstanding Cloud Host, physical cloud hosts, and ULB); “Specific resources within the subnet” means that this rule only applies to the selected resources (specifying high-availability UDB is not supported), and does not apply to unselected resources within the subnet.
Note: After creating a network ACL, the system will automatically add a default outbound rule and a default inbound rule.
The default outbound rule is to allow outbound traffic for all protocols and ports.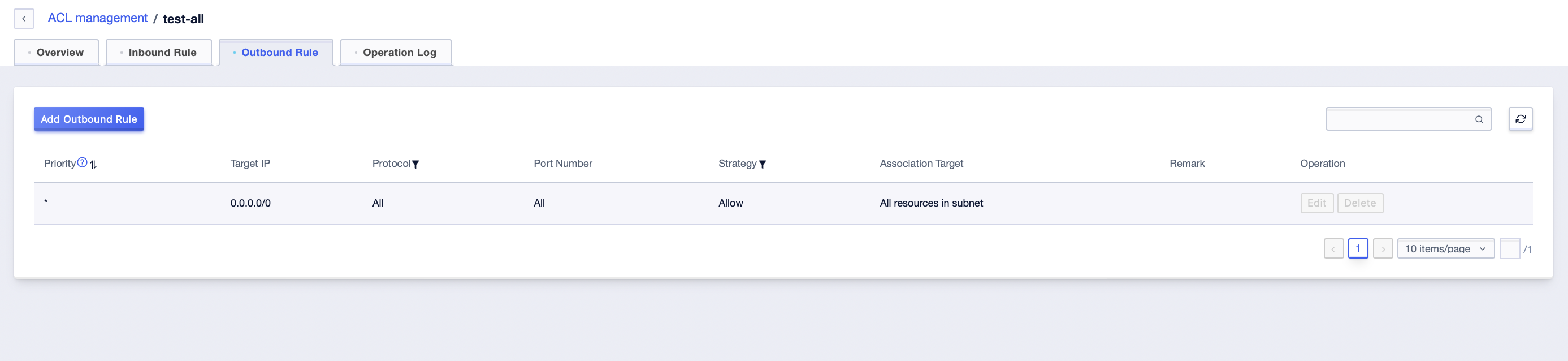
The default inbound rule is to allow inbound traffic for all protocols and ports.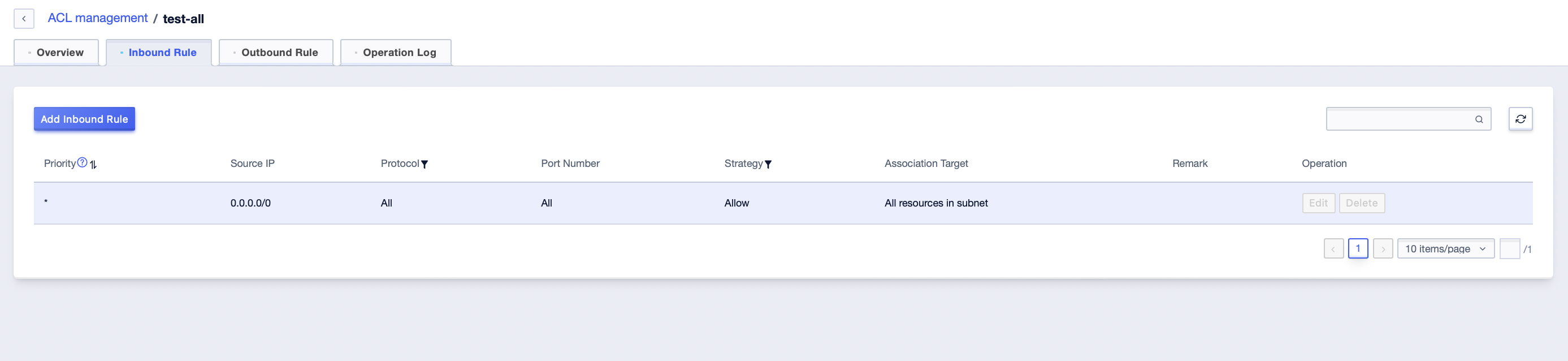
Default rules cannot be edited or deleted, they exist at the creation of the ACL.
Default rules have the lowest priority, and you can override the default rules by adding rules with higher priority.
Product Quota
Each network ACL quota is as follows (excluding default rules)
| Name | Quota |
|---|---|
| Number of Outbound Rules | 100 |
| Number of Inbound Rules | 100 |